Cloud Security
Posture Management (CSPM)
Continuously Assess, Detect, and Remediate Security and Compliance Risks Across Multi-Cloud Infrastructure
A 100% agentless CSPM helping enforce cloud security best practices, automate cloud security incident response and stay compliant with multiple compliance standards.
"99 Percent Of All Misconfigurations In The Public Cloud Go Unreported"
What is CSPM?
CSPMs are solutions that empowers companies to automate cloud security management across diverse cloud infrastructures. CSPMs continuously monitor enterprise cloud environments to identify and remediate security issues automatically.

CARTA Driven Approach to Cloud Security
C3M Cloud Control has adopted the Continuous Adaptive Risk and Trust Assessment (CARTA) approach as its foundation to continuously assess, detect, govern, and remediate misconfigurations and threats in your cloud environments.
Critical challenges to your Cloud Security
How do I gain visibility into resources deployed in the cloud?
What are the resources violating security best practices?
How do you automate cloud incident response and avoid alert fatigue?
How do I ensure my cloud usage is in compliance with the applicable security regulations and standards?
How do I identify vulnerabilities and remediate them?
Who made the configuration changes?
- Multi Cloud Visibility and Inventory
- Extensive Compliance Monitoring to Industry Standards
- Enforce Cloud Security Best Practices
- Detect and Prevent Cloud Misconfigurations
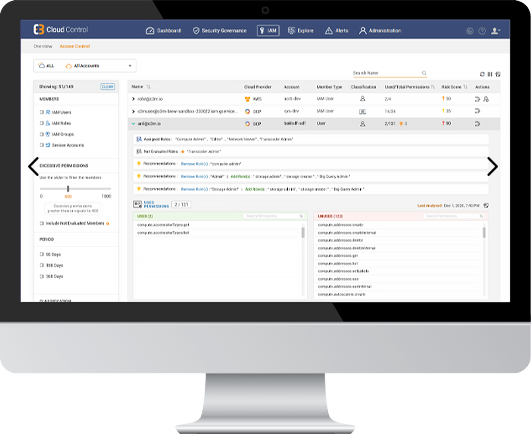
- Automate response to Cloud Incidents
- Cloud Security and Compliance Posture Reporting
- Auditing and Forensic capabilities
- Create Custom Policies
C3M Cloud Control is the only cloud native CSPM solution that unifies and correlates cloud security intelligence providing a consolidated management interface for your cloud.
Complete Cloud Visibility
Comprehensive asset inventory capabilities on multi-cloud. Get complete visibility into your Compute, Network, Storage and IAM components in the cloud.
Policy Governance
Define and enforce cloud security policies based on security requirements by enforcing C3M’s out-of-the-box CSPM policies or create custom policies using our CQL engine.
Response Automation
Leverage SOAR capabilities via C3M Playbooks to automate cloud incident response and provide a flexible, customizable, and extensible framework that can support multiple remediations across AWS, GCP, and Azure.
Contextual Reporting
Generate customisable one-off or pre-scheduled and predefined reports or summary reports that can be submitted to the executive leadership to give them an overview of the overall cloud security posture.
Query Language
Gain real-time security and operational intelligence about the multi-cloud infrastructure or check the configuration of various resources using Cloud Query Language (CQL). CQL can also be used to create and enforce custom policies specific to an enterprise.
Security Posture Summary
Contextual insights into the entire cloud security posture, all resources, alerts, and compliance status across multi-cloud environments are available through simple and easy to use dashboards.
Resources

Blog
Are your IAM Access Keys Safe?
The Breach The last few months have seen multiple data breaches across organisations in the retail, stock brokerage, restaurant chain, FinTech space etc in India.

Blog
Public Cloud Infrastructure attracts Crypto miners like bees to beehives
While talking to many of our customers, prospects, and partners who have established cloud strategies, a common pattern is evolving. The majority of them have

Blog
On 15th January we released C3M Cloud Control 4.0
The key highlights of this release are: CSPM (Cloud Security & Posture Management): User Management RBAC – The support for RBAC controls at the account

